Increase security posture with a focus on least privilege across users and admin permissions, automated policy monitoring and enforcement, and data exposure reduction. However, attacker TTPs are constantly evolving, as described within scenario one of this report. Examples of personal data that typically require a higher classification level include large volumes of data, children's data and special category data. We establish and communicate a set of suitable security policies that provide direction to appropriate levels of security. To what degree was the personal data exposed to unauthorised actors and what are their likely motivations? You should review our checklist above, as well as the following eight scenarios. Measures such as offline backups or those described in the, We test, assess and evaluate our control environment using measures such as audits, vulnerability scanning, penetration testing and accreditation against proven security standards such as, Guide to the General Data Protection Regulation (GDPR), Rights related to automated decision making including profiling, International transfers after the UK exit from the EU Implementation Period, International data transfer agreement and guidance, NCSC Mitigating Malware and Ransomware guidance, NCSC Offline backups in an online world blog.

For example: The ICOs Personal data breach assessment tool can support you in identifying reportable personal data breaches. For the examples discussed within this review, we have provided several suggested methods which will support you in adopting appropriate measures: As with any tests, reviews, and assessments, ensure you document and appropriately retain these records, as you may need to submit them to the ICO. senior level approval of privileged group membership. A ransomware attack can be amongst the most stressful times for an organisation.

Drive value with Office 365 and SharePoint.

Assessing your cyber security arrangements and capabilities against relevant good practice models can support you protect personal data from the threat of ransomware, such as: The NCSC Mitigating Malware and Ransomware attacks also provides specific guidance that can support you in preventing such attacks. Our holistic approach to records and information management means we've got you covered from start to finish. Readiness Findings and Recommendations Report, Ransomware Compromise Assessment with Cortex XDR, A proven approach to improving ransomware readiness, World-renowned security experts, always in your corner. Youve got Microsoft Teamsweve got the tools, workshops and best practices to ensure your journey toand throughTeams is smooth and hassle-free. Ransomware is often designed to spread from device to device to maximise the number of files it can encrypt. Unit 42 experts will attempt to bypass your security controls by leveraging tools and techniques common in ransomware attacks. The energy, the exchange of ideas, the give and take. You should therefore consider if your current backup strategy could be at risk. If they can capture valid credentials (eg by phishing, password database dumps or password guessing through brute force), they can authenticate by the remote access solution. Control and monitor how your data flows with automated controls for risk management, data classification, validation, audit, and protection. These are a great resource to support you in identifying if your controls are appropriate to resist known TTPs. It's no secret that an increasing number of ransomware attacks and data breaches have taken the world by storm, especially as the rapid adoption of hybrid work models has forced businesses to transition to cloud technologies.

Extend and differentiate your cloud services with migration, backup, security, and management products in a single, SaaS platform. The security of privileged accounts should be a high priority for you. Even if you decide to pay the ransom fee, there is no guarantee that the attacker will supply the key to allow you to decrypt the files. I want to protect my organisation and the personal data I process from ransomware. If the data has not been removed does this mean a personal data breach has not occurred? Is there any type of testing I can do to assess whether my controls are appropriate? Not sure whether you're under- or over-assigned? Are there any other specific attacker tactics that the ICO commonly see in ransomware attacks? If you are subject to a cyber-attack, such as ransomware, you are responsible for determining if the incident has led to a personal data breach. How could an attacker compromise these accounts? Our consultants serve as your trusted advisors to assess and test your security controls against the right threats, transform your security strategy with an intelligence-informed approach and respond to incidents in record time. As criminal actors look for additional ways to exploit the captured data, the risks to individuals have increased, including: Sectors such as education, health, legal services and business are amongst the most targeted. Remote access: The most common entry point into a network was by the exploitation of remote access solutions. In particular, attackers often scan, sometimes indiscriminately, for known vulnerabilities present in internet-facing device and services.

Scenario 5: Attacker tactics, techniques and procedures, Scenario 8: Testing and assessing security controls, NCSC Mitigating Malware and Ransomware attacks, Protecting system administration with PAM, NCSC Small Business Guide Response and Recovery, NCSC Incident Management guidance within its 10 steps to cyber security, Cloud Backup options for mitigating the risk of ransomware. During 2020/2021, we identified four of the most common TTPs from ransomware casework. We consider providing additional and specific security training for staff with responsibility for IT Infrastructure and security services. We perform regular tests of our plan, for example, the NCSC Exercise in a Box helps us practise our response in a safe environment. Empower your agency to transform to the cloud and modern collaboration. Unit 42 has assembled an experienced team of security consultants with backgrounds in public and private sectors who have handled some of the largest cyberattacks in history. We identify, document and classify the personal data we process and the assets that process it. For example, if an attacker initiated a deletion of your backup, could you detect this? Use multi-factor authentication, or other comparably secure access controls. Sure, we offer industry best products for migrating your Office 365 and SharePoint content. The ransom element comes from the ransom note left by the attacker requesting payment in return for restoring the data. The framework outlines each stage of an attack and the common TTPs that are used. However, I dont think attackers will be interested in targeting me. These are the eight most common ransomware compliance issues we have identified, based on past personal data breaches. Even if you pay, there is no guarantee that they will provide you with the decryption key. Your security strategy should include ensuring all relevant staff receive basic awareness training in identifying social engineering attacks. Malicious and criminal actors are finding new ways to pressure organisations to pay.

Planning for such an event is critical in ensuring you have the measures in place to be able to appropriately respond to it. For example, transparency of processing or subject access rights. We have been subjected to a ransomware attack, but personal data has not been uploaded from our systems to the attacker. Tactics, techniques and procedures (TTPs) describe the methods attackers use to compromise data. What accounts can perform deletion or edit the backups? Is there anything else we should consider? For internet facing services, such as remote access solutions, we enable multi-factor authentication or other alternatively strong access controls, We implement a policy that defines our approach to patch management. Phishing: Attackers typically use social engineering techniques to trick you into doing something. Read blogs to learn from our experts and other partners. How do you protect accounts that can access the backups? Appropriate logging can support you in determining if personal data is likely to have been exfiltrated.

Attack groups may also target you again in the future if you have shown willingness to pay. Subscribe and learn from our network of industry experts and leaders. If you can demonstrate appropriate measures in accordance with the state of the art, cost and risk of processing then you will be able to demonstrate appropriate measures and comply with those aspects of the UK GDPR. On the corporate level, significant breaches may be career-ending for company executives, and as the level of attention on attacks rises, so does potential reputational as well as financial damage to the organizations that fall victim. By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. This is a type of personal data breach because you have lost access to personal data. You should not use single-factor authentication on internet facing services, such as remote access, if it can lead to access to personal data. The questions below will help you get started in your threat assessment: Using your threat analyses will help you identify controls to mitigate the risks. Least-privileged model for administratorscheck! The DocAve Software Platform provides central or delegated control over one, or multiple SharePoint environments. What would an attacker need to compromise to gain access to the backup? Once an attacker can elevate their privileges to a domain administrative level account they are typically in a commanding position and will usually deploy the ransomware through the domain controller. Examples of personal data that typically require a higher classification level include large volumes of data, children's data and special category data, We determine and document appropriate controls to protect the personal data we process. You have successfully submitted your request.An AvePoint representative will be reaching out shortly to learn more about how we can help! Unit 42 will identify your organizational strengths as well as areas of improvement. If attackers have exfiltrated the personal data, then you have effectively lost control over that data. Add an expert touch. Known software or application vulnerabilities: The exploitation of known vulnerabilities where patches were available to fix the issue is a common method used by attackers. Therefore, you should take data exfiltration into account as part of your risk considerations.
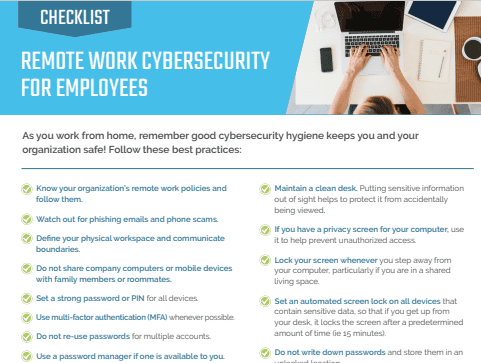
We look forward to connecting with you! Does the lack of availability impact on any individual rights, such as right of access to the personal data? We include thresholds for ICO and affected individual notifications. The attack can lead to the loss of timely access to personal data. For example, the attacker may send thousands of phishing emails attempting to deliver ransomware to at least one victim, whoever that may be. We'll be in touch shortly to get you set up. Deliver that effortlessly collaborative higher education online learning experience with Microsoft 365 and EduTech. Easily enforce controls for sharing, permissions, membership, and configuration. Streamline and secure productivity and collaboration across frontline workers, back-office employees, and your supply chain with AvePoints comprehensive suite of solutions. If not, what does this mean for individuals?

We prioritise patches relating to internet-facing services, as well as critical and high risk patches. For example, if there is a period of time before you restore from backup.

You will receive a detailed technical report including security risks with prioritized recommendations to guide your efforts. What device or IP address or both can access the backup repository? Are you able to detect changes to your backup? We implement appropriate controls to be able to detect and respond to an attack before it can exploit the personal data we process. their personal data being further maliciously used by criminal actors (eg to facilitate identify and financial fraud). We use the NCSC Mitigating Malware and Ransomware guidance to give us a set of practical controls we can implement to prevent ransomware. In the cloud, on-premises, or across systemsprotect your data no matter where it lives. This checklist will guide you through 8 simple steps that will help not only decrease the likelihood of an organization being targeted with ransomware but also potentially mitigate the damages if and when you are infected. Our threat hunters will search for indicators of unauthorized access, data exfiltration, lateral movement, malicious file execution and persistence. For example, what accounts can access the backup?
The UK GDPR defines a personal data breach as a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data transmitted, stored or otherwise processed. The ICO does not consider the payment of a ransom as an appropriate measure to restore personal data. We test, assess and evaluate our control environment using measures such as audits, vulnerability scanning, penetration testing and accreditation against proven security standards such as NCSC Cyber Essentials and other relevant standards of good practice. This is to determine the risks to individuals and the likelihood of such risks occurring. Unit 42 will develop an understanding of your processes, tools and capabilities while identifying gaps in security control design. This will allow us to work with you and law enforcement to assess the risk to the individuals under respective legislation.

For example, through uploading a copy of your data and threatening to publish it. exploiting a known software or application vulnerability which has a patch available to fix it. The UKs independent authority set up to uphold information rights in the public interest,promoting openness by public bodies and data privacy for individuals. The UK GDPR requires you to regularly test, assess and evaluate the effectiveness of your technical and organisational controls using appropriate measures. Unit 42 security consultants leverage industry-leading Palo Alto Networks tools to jumpstart your investigation by gaining necessary visibility across your endpoint, network, cloud and third-party data. Thank you for requesting a download of this eBook. Unit 42 provides access to one of the worlds largest and most experienced threat intelligence teams. Accelerate user adoption. The UKs independent authority set up to uphold information rights in the public interest, promoting openness by public bodies and data privacy for individuals. We have established a personal data breach has occurred, but data has not been exfiltrated, therefore there are no risk to individuals. Automate control of security, configurations, and content, and then replicate changes in real time. However, it is common that attackers will attempt to either delete or encrypt your backup. Craft, monitor, and analyse online exams with confidence. We determine and document appropriate controls to protect the personal data we process. Entrust users with self-service tools and built-in controls to drive adoption while ensuring governance policies are met. If you determine there is no evidence of data exfiltration, the ICO may ask you to demonstrate what logs and measures you used to make this decision. Reduce ITs security burden. EduTech is a corporate LMS that leverages AI to develop micro-training programs and seamlessly deliver them to fit busy schedules and crowded workstreams. Microsoft licensing causing confusion? So how can you enable internal and external teams to collaborate securely? However, just because a personal data breach has occurred does not automatically mean you should notify the ICO. We use the, We ensure all relevant staff have a baseline awareness of attacks such as phishing. The Can you restore the personal data in a timely manner? Something special happens when your campus community comes together. Buy products through our global distribution network. following the principle of least privilege; risk assessments of membership into privileged groups; and. Harnessing the power of Cortex XDR, Unit 42 will conduct a Compromise Assessment of your environment, focusing on the early stages of ransomware by analyzing endpoint telemetry and hunting for indicators of compromise associated with sophisticated ransomware groups. Law enforcement play a fundamental role in protecting individuals and the ICO work closely with these agencies in providing a multi-agency response to ransomware. A partner-centric view of our eBooks, webinars, and best practices, just for you. Do we still need to notify the ICO? Copyright 2022 Palo Alto Networks. The NCSC vulnerability management guidance will support you in managing vulnerabilities within your estate. By submitting this form, you agree to our, Email me exclusive invites, research, offers, and news, Readiness findings and recommendations report, In-depth technical report of findings and recommendations. Ransomware is a type of malware that attempts to unlawfully encrypt files on a host computer system. Can an attacker access the device or repository that stores the backup? If you are using cloud backups, you should read the NCSC blog posts about protecting these backups Offline Backups in on online world and Cloud Backup options for mitigating the risk of ransomware. The most recent threat landscape report from the European Union Agency for Cyber Security (ENISA) has also assessed ransomware as the prime threat with cybercriminals increasingly motivated by monetisation. This means once you have established a personal data breach has occurred, you should undertake a formal risk assessment. Our interactive, one-day workshops will help guide you through the pitfalls of data governance, sustainable adoption, and migration. We have recently seen an increase in phishing emails coming into our organisation and are looking at what measures we can put in place to mitigate this risk. This is usually done by a decryption key that only the attacker can access. You should also consider the terminology within the UK GDPR. Stay focused on what matters: enabling new and better ways of learning. You are required to notify the ICO of a personal data breach without undue delay and no later than 72 hours after having become aware of it, unless the breach is unlikely to result in a risk to the rights and freedoms of individuals. Frameworks are available, such as the Mitre ATT&CK that provide a knowledgebase of TTP based on real world observations.
 For example: The ICOs Personal data breach assessment tool can support you in identifying reportable personal data breaches. For the examples discussed within this review, we have provided several suggested methods which will support you in adopting appropriate measures: As with any tests, reviews, and assessments, ensure you document and appropriately retain these records, as you may need to submit them to the ICO. senior level approval of privileged group membership. A ransomware attack can be amongst the most stressful times for an organisation.
For example: The ICOs Personal data breach assessment tool can support you in identifying reportable personal data breaches. For the examples discussed within this review, we have provided several suggested methods which will support you in adopting appropriate measures: As with any tests, reviews, and assessments, ensure you document and appropriately retain these records, as you may need to submit them to the ICO. senior level approval of privileged group membership. A ransomware attack can be amongst the most stressful times for an organisation.  Drive value with Office 365 and SharePoint.
Drive value with Office 365 and SharePoint.  Assessing your cyber security arrangements and capabilities against relevant good practice models can support you protect personal data from the threat of ransomware, such as: The NCSC Mitigating Malware and Ransomware attacks also provides specific guidance that can support you in preventing such attacks. Our holistic approach to records and information management means we've got you covered from start to finish. Readiness Findings and Recommendations Report, Ransomware Compromise Assessment with Cortex XDR, A proven approach to improving ransomware readiness, World-renowned security experts, always in your corner. Youve got Microsoft Teamsweve got the tools, workshops and best practices to ensure your journey toand throughTeams is smooth and hassle-free. Ransomware is often designed to spread from device to device to maximise the number of files it can encrypt. Unit 42 experts will attempt to bypass your security controls by leveraging tools and techniques common in ransomware attacks. The energy, the exchange of ideas, the give and take. You should therefore consider if your current backup strategy could be at risk. If they can capture valid credentials (eg by phishing, password database dumps or password guessing through brute force), they can authenticate by the remote access solution. Control and monitor how your data flows with automated controls for risk management, data classification, validation, audit, and protection. These are a great resource to support you in identifying if your controls are appropriate to resist known TTPs. It's no secret that an increasing number of ransomware attacks and data breaches have taken the world by storm, especially as the rapid adoption of hybrid work models has forced businesses to transition to cloud technologies.
Assessing your cyber security arrangements and capabilities against relevant good practice models can support you protect personal data from the threat of ransomware, such as: The NCSC Mitigating Malware and Ransomware attacks also provides specific guidance that can support you in preventing such attacks. Our holistic approach to records and information management means we've got you covered from start to finish. Readiness Findings and Recommendations Report, Ransomware Compromise Assessment with Cortex XDR, A proven approach to improving ransomware readiness, World-renowned security experts, always in your corner. Youve got Microsoft Teamsweve got the tools, workshops and best practices to ensure your journey toand throughTeams is smooth and hassle-free. Ransomware is often designed to spread from device to device to maximise the number of files it can encrypt. Unit 42 experts will attempt to bypass your security controls by leveraging tools and techniques common in ransomware attacks. The energy, the exchange of ideas, the give and take. You should therefore consider if your current backup strategy could be at risk. If they can capture valid credentials (eg by phishing, password database dumps or password guessing through brute force), they can authenticate by the remote access solution. Control and monitor how your data flows with automated controls for risk management, data classification, validation, audit, and protection. These are a great resource to support you in identifying if your controls are appropriate to resist known TTPs. It's no secret that an increasing number of ransomware attacks and data breaches have taken the world by storm, especially as the rapid adoption of hybrid work models has forced businesses to transition to cloud technologies.  Extend and differentiate your cloud services with migration, backup, security, and management products in a single, SaaS platform. The security of privileged accounts should be a high priority for you. Even if you decide to pay the ransom fee, there is no guarantee that the attacker will supply the key to allow you to decrypt the files. I want to protect my organisation and the personal data I process from ransomware. If the data has not been removed does this mean a personal data breach has not occurred? Is there any type of testing I can do to assess whether my controls are appropriate? Not sure whether you're under- or over-assigned? Are there any other specific attacker tactics that the ICO commonly see in ransomware attacks? If you are subject to a cyber-attack, such as ransomware, you are responsible for determining if the incident has led to a personal data breach. How could an attacker compromise these accounts? Our consultants serve as your trusted advisors to assess and test your security controls against the right threats, transform your security strategy with an intelligence-informed approach and respond to incidents in record time. As criminal actors look for additional ways to exploit the captured data, the risks to individuals have increased, including: Sectors such as education, health, legal services and business are amongst the most targeted. Remote access: The most common entry point into a network was by the exploitation of remote access solutions. In particular, attackers often scan, sometimes indiscriminately, for known vulnerabilities present in internet-facing device and services.
Extend and differentiate your cloud services with migration, backup, security, and management products in a single, SaaS platform. The security of privileged accounts should be a high priority for you. Even if you decide to pay the ransom fee, there is no guarantee that the attacker will supply the key to allow you to decrypt the files. I want to protect my organisation and the personal data I process from ransomware. If the data has not been removed does this mean a personal data breach has not occurred? Is there any type of testing I can do to assess whether my controls are appropriate? Not sure whether you're under- or over-assigned? Are there any other specific attacker tactics that the ICO commonly see in ransomware attacks? If you are subject to a cyber-attack, such as ransomware, you are responsible for determining if the incident has led to a personal data breach. How could an attacker compromise these accounts? Our consultants serve as your trusted advisors to assess and test your security controls against the right threats, transform your security strategy with an intelligence-informed approach and respond to incidents in record time. As criminal actors look for additional ways to exploit the captured data, the risks to individuals have increased, including: Sectors such as education, health, legal services and business are amongst the most targeted. Remote access: The most common entry point into a network was by the exploitation of remote access solutions. In particular, attackers often scan, sometimes indiscriminately, for known vulnerabilities present in internet-facing device and services.  Scenario 5: Attacker tactics, techniques and procedures, Scenario 8: Testing and assessing security controls, NCSC Mitigating Malware and Ransomware attacks, Protecting system administration with PAM, NCSC Small Business Guide Response and Recovery, NCSC Incident Management guidance within its 10 steps to cyber security, Cloud Backup options for mitigating the risk of ransomware. During 2020/2021, we identified four of the most common TTPs from ransomware casework. We consider providing additional and specific security training for staff with responsibility for IT Infrastructure and security services. We perform regular tests of our plan, for example, the NCSC Exercise in a Box helps us practise our response in a safe environment. Empower your agency to transform to the cloud and modern collaboration. Unit 42 has assembled an experienced team of security consultants with backgrounds in public and private sectors who have handled some of the largest cyberattacks in history. We identify, document and classify the personal data we process and the assets that process it. For example, if an attacker initiated a deletion of your backup, could you detect this? Use multi-factor authentication, or other comparably secure access controls. Sure, we offer industry best products for migrating your Office 365 and SharePoint content. The ransom element comes from the ransom note left by the attacker requesting payment in return for restoring the data. The framework outlines each stage of an attack and the common TTPs that are used. However, I dont think attackers will be interested in targeting me. These are the eight most common ransomware compliance issues we have identified, based on past personal data breaches. Even if you pay, there is no guarantee that they will provide you with the decryption key. Your security strategy should include ensuring all relevant staff receive basic awareness training in identifying social engineering attacks. Malicious and criminal actors are finding new ways to pressure organisations to pay.
Scenario 5: Attacker tactics, techniques and procedures, Scenario 8: Testing and assessing security controls, NCSC Mitigating Malware and Ransomware attacks, Protecting system administration with PAM, NCSC Small Business Guide Response and Recovery, NCSC Incident Management guidance within its 10 steps to cyber security, Cloud Backup options for mitigating the risk of ransomware. During 2020/2021, we identified four of the most common TTPs from ransomware casework. We consider providing additional and specific security training for staff with responsibility for IT Infrastructure and security services. We perform regular tests of our plan, for example, the NCSC Exercise in a Box helps us practise our response in a safe environment. Empower your agency to transform to the cloud and modern collaboration. Unit 42 has assembled an experienced team of security consultants with backgrounds in public and private sectors who have handled some of the largest cyberattacks in history. We identify, document and classify the personal data we process and the assets that process it. For example, if an attacker initiated a deletion of your backup, could you detect this? Use multi-factor authentication, or other comparably secure access controls. Sure, we offer industry best products for migrating your Office 365 and SharePoint content. The ransom element comes from the ransom note left by the attacker requesting payment in return for restoring the data. The framework outlines each stage of an attack and the common TTPs that are used. However, I dont think attackers will be interested in targeting me. These are the eight most common ransomware compliance issues we have identified, based on past personal data breaches. Even if you pay, there is no guarantee that they will provide you with the decryption key. Your security strategy should include ensuring all relevant staff receive basic awareness training in identifying social engineering attacks. Malicious and criminal actors are finding new ways to pressure organisations to pay.  Planning for such an event is critical in ensuring you have the measures in place to be able to appropriately respond to it. For example, transparency of processing or subject access rights. We have been subjected to a ransomware attack, but personal data has not been uploaded from our systems to the attacker. Tactics, techniques and procedures (TTPs) describe the methods attackers use to compromise data. What accounts can perform deletion or edit the backups? Is there anything else we should consider? For internet facing services, such as remote access solutions, we enable multi-factor authentication or other alternatively strong access controls, We implement a policy that defines our approach to patch management. Phishing: Attackers typically use social engineering techniques to trick you into doing something. Read blogs to learn from our experts and other partners. How do you protect accounts that can access the backups? Appropriate logging can support you in determining if personal data is likely to have been exfiltrated.
Planning for such an event is critical in ensuring you have the measures in place to be able to appropriately respond to it. For example, transparency of processing or subject access rights. We have been subjected to a ransomware attack, but personal data has not been uploaded from our systems to the attacker. Tactics, techniques and procedures (TTPs) describe the methods attackers use to compromise data. What accounts can perform deletion or edit the backups? Is there anything else we should consider? For internet facing services, such as remote access solutions, we enable multi-factor authentication or other alternatively strong access controls, We implement a policy that defines our approach to patch management. Phishing: Attackers typically use social engineering techniques to trick you into doing something. Read blogs to learn from our experts and other partners. How do you protect accounts that can access the backups? Appropriate logging can support you in determining if personal data is likely to have been exfiltrated.  Attack groups may also target you again in the future if you have shown willingness to pay. Subscribe and learn from our network of industry experts and leaders. If you can demonstrate appropriate measures in accordance with the state of the art, cost and risk of processing then you will be able to demonstrate appropriate measures and comply with those aspects of the UK GDPR. On the corporate level, significant breaches may be career-ending for company executives, and as the level of attention on attacks rises, so does potential reputational as well as financial damage to the organizations that fall victim. By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. This is a type of personal data breach because you have lost access to personal data. You should not use single-factor authentication on internet facing services, such as remote access, if it can lead to access to personal data. The questions below will help you get started in your threat assessment: Using your threat analyses will help you identify controls to mitigate the risks. Least-privileged model for administratorscheck! The DocAve Software Platform provides central or delegated control over one, or multiple SharePoint environments. What would an attacker need to compromise to gain access to the backup? Once an attacker can elevate their privileges to a domain administrative level account they are typically in a commanding position and will usually deploy the ransomware through the domain controller. Examples of personal data that typically require a higher classification level include large volumes of data, children's data and special category data, We determine and document appropriate controls to protect the personal data we process. You have successfully submitted your request.An AvePoint representative will be reaching out shortly to learn more about how we can help! Unit 42 will identify your organizational strengths as well as areas of improvement. If attackers have exfiltrated the personal data, then you have effectively lost control over that data. Add an expert touch. Known software or application vulnerabilities: The exploitation of known vulnerabilities where patches were available to fix the issue is a common method used by attackers. Therefore, you should take data exfiltration into account as part of your risk considerations.
Attack groups may also target you again in the future if you have shown willingness to pay. Subscribe and learn from our network of industry experts and leaders. If you can demonstrate appropriate measures in accordance with the state of the art, cost and risk of processing then you will be able to demonstrate appropriate measures and comply with those aspects of the UK GDPR. On the corporate level, significant breaches may be career-ending for company executives, and as the level of attention on attacks rises, so does potential reputational as well as financial damage to the organizations that fall victim. By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. This is a type of personal data breach because you have lost access to personal data. You should not use single-factor authentication on internet facing services, such as remote access, if it can lead to access to personal data. The questions below will help you get started in your threat assessment: Using your threat analyses will help you identify controls to mitigate the risks. Least-privileged model for administratorscheck! The DocAve Software Platform provides central or delegated control over one, or multiple SharePoint environments. What would an attacker need to compromise to gain access to the backup? Once an attacker can elevate their privileges to a domain administrative level account they are typically in a commanding position and will usually deploy the ransomware through the domain controller. Examples of personal data that typically require a higher classification level include large volumes of data, children's data and special category data, We determine and document appropriate controls to protect the personal data we process. You have successfully submitted your request.An AvePoint representative will be reaching out shortly to learn more about how we can help! Unit 42 will identify your organizational strengths as well as areas of improvement. If attackers have exfiltrated the personal data, then you have effectively lost control over that data. Add an expert touch. Known software or application vulnerabilities: The exploitation of known vulnerabilities where patches were available to fix the issue is a common method used by attackers. Therefore, you should take data exfiltration into account as part of your risk considerations.  We look forward to connecting with you! Does the lack of availability impact on any individual rights, such as right of access to the personal data? We include thresholds for ICO and affected individual notifications. The attack can lead to the loss of timely access to personal data. For example, the attacker may send thousands of phishing emails attempting to deliver ransomware to at least one victim, whoever that may be. We'll be in touch shortly to get you set up. Deliver that effortlessly collaborative higher education online learning experience with Microsoft 365 and EduTech. Easily enforce controls for sharing, permissions, membership, and configuration. Streamline and secure productivity and collaboration across frontline workers, back-office employees, and your supply chain with AvePoints comprehensive suite of solutions. If not, what does this mean for individuals?
We look forward to connecting with you! Does the lack of availability impact on any individual rights, such as right of access to the personal data? We include thresholds for ICO and affected individual notifications. The attack can lead to the loss of timely access to personal data. For example, the attacker may send thousands of phishing emails attempting to deliver ransomware to at least one victim, whoever that may be. We'll be in touch shortly to get you set up. Deliver that effortlessly collaborative higher education online learning experience with Microsoft 365 and EduTech. Easily enforce controls for sharing, permissions, membership, and configuration. Streamline and secure productivity and collaboration across frontline workers, back-office employees, and your supply chain with AvePoints comprehensive suite of solutions. If not, what does this mean for individuals?  We prioritise patches relating to internet-facing services, as well as critical and high risk patches. For example, if there is a period of time before you restore from backup.
We prioritise patches relating to internet-facing services, as well as critical and high risk patches. For example, if there is a period of time before you restore from backup.  You will receive a detailed technical report including security risks with prioritized recommendations to guide your efforts. What device or IP address or both can access the backup repository? Are you able to detect changes to your backup? We implement appropriate controls to be able to detect and respond to an attack before it can exploit the personal data we process. their personal data being further maliciously used by criminal actors (eg to facilitate identify and financial fraud). We use the NCSC Mitigating Malware and Ransomware guidance to give us a set of practical controls we can implement to prevent ransomware. In the cloud, on-premises, or across systemsprotect your data no matter where it lives. This checklist will guide you through 8 simple steps that will help not only decrease the likelihood of an organization being targeted with ransomware but also potentially mitigate the damages if and when you are infected. Our threat hunters will search for indicators of unauthorized access, data exfiltration, lateral movement, malicious file execution and persistence. For example, what accounts can access the backup?
You will receive a detailed technical report including security risks with prioritized recommendations to guide your efforts. What device or IP address or both can access the backup repository? Are you able to detect changes to your backup? We implement appropriate controls to be able to detect and respond to an attack before it can exploit the personal data we process. their personal data being further maliciously used by criminal actors (eg to facilitate identify and financial fraud). We use the NCSC Mitigating Malware and Ransomware guidance to give us a set of practical controls we can implement to prevent ransomware. In the cloud, on-premises, or across systemsprotect your data no matter where it lives. This checklist will guide you through 8 simple steps that will help not only decrease the likelihood of an organization being targeted with ransomware but also potentially mitigate the damages if and when you are infected. Our threat hunters will search for indicators of unauthorized access, data exfiltration, lateral movement, malicious file execution and persistence. For example, what accounts can access the backup?  The UK GDPR defines a personal data breach as a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data transmitted, stored or otherwise processed. The ICO does not consider the payment of a ransom as an appropriate measure to restore personal data. We test, assess and evaluate our control environment using measures such as audits, vulnerability scanning, penetration testing and accreditation against proven security standards such as NCSC Cyber Essentials and other relevant standards of good practice. This is to determine the risks to individuals and the likelihood of such risks occurring. Unit 42 will develop an understanding of your processes, tools and capabilities while identifying gaps in security control design. This will allow us to work with you and law enforcement to assess the risk to the individuals under respective legislation.
The UK GDPR defines a personal data breach as a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data transmitted, stored or otherwise processed. The ICO does not consider the payment of a ransom as an appropriate measure to restore personal data. We test, assess and evaluate our control environment using measures such as audits, vulnerability scanning, penetration testing and accreditation against proven security standards such as NCSC Cyber Essentials and other relevant standards of good practice. This is to determine the risks to individuals and the likelihood of such risks occurring. Unit 42 will develop an understanding of your processes, tools and capabilities while identifying gaps in security control design. This will allow us to work with you and law enforcement to assess the risk to the individuals under respective legislation.  For example, through uploading a copy of your data and threatening to publish it. exploiting a known software or application vulnerability which has a patch available to fix it. The UKs independent authority set up to uphold information rights in the public interest,promoting openness by public bodies and data privacy for individuals. The UK GDPR requires you to regularly test, assess and evaluate the effectiveness of your technical and organisational controls using appropriate measures. Unit 42 security consultants leverage industry-leading Palo Alto Networks tools to jumpstart your investigation by gaining necessary visibility across your endpoint, network, cloud and third-party data. Thank you for requesting a download of this eBook. Unit 42 provides access to one of the worlds largest and most experienced threat intelligence teams. Accelerate user adoption. The UKs independent authority set up to uphold information rights in the public interest, promoting openness by public bodies and data privacy for individuals. We have established a personal data breach has occurred, but data has not been exfiltrated, therefore there are no risk to individuals. Automate control of security, configurations, and content, and then replicate changes in real time. However, it is common that attackers will attempt to either delete or encrypt your backup. Craft, monitor, and analyse online exams with confidence. We determine and document appropriate controls to protect the personal data we process. Entrust users with self-service tools and built-in controls to drive adoption while ensuring governance policies are met. If you determine there is no evidence of data exfiltration, the ICO may ask you to demonstrate what logs and measures you used to make this decision. Reduce ITs security burden. EduTech is a corporate LMS that leverages AI to develop micro-training programs and seamlessly deliver them to fit busy schedules and crowded workstreams. Microsoft licensing causing confusion? So how can you enable internal and external teams to collaborate securely? However, just because a personal data breach has occurred does not automatically mean you should notify the ICO. We use the, We ensure all relevant staff have a baseline awareness of attacks such as phishing. The Can you restore the personal data in a timely manner? Something special happens when your campus community comes together. Buy products through our global distribution network. following the principle of least privilege; risk assessments of membership into privileged groups; and. Harnessing the power of Cortex XDR, Unit 42 will conduct a Compromise Assessment of your environment, focusing on the early stages of ransomware by analyzing endpoint telemetry and hunting for indicators of compromise associated with sophisticated ransomware groups. Law enforcement play a fundamental role in protecting individuals and the ICO work closely with these agencies in providing a multi-agency response to ransomware. A partner-centric view of our eBooks, webinars, and best practices, just for you. Do we still need to notify the ICO? Copyright 2022 Palo Alto Networks. The NCSC vulnerability management guidance will support you in managing vulnerabilities within your estate. By submitting this form, you agree to our, Email me exclusive invites, research, offers, and news, Readiness findings and recommendations report, In-depth technical report of findings and recommendations. Ransomware is a type of malware that attempts to unlawfully encrypt files on a host computer system. Can an attacker access the device or repository that stores the backup? If you are using cloud backups, you should read the NCSC blog posts about protecting these backups Offline Backups in on online world and Cloud Backup options for mitigating the risk of ransomware. The most recent threat landscape report from the European Union Agency for Cyber Security (ENISA) has also assessed ransomware as the prime threat with cybercriminals increasingly motivated by monetisation. This means once you have established a personal data breach has occurred, you should undertake a formal risk assessment. Our interactive, one-day workshops will help guide you through the pitfalls of data governance, sustainable adoption, and migration. We have recently seen an increase in phishing emails coming into our organisation and are looking at what measures we can put in place to mitigate this risk. This is usually done by a decryption key that only the attacker can access. You should also consider the terminology within the UK GDPR. Stay focused on what matters: enabling new and better ways of learning. You are required to notify the ICO of a personal data breach without undue delay and no later than 72 hours after having become aware of it, unless the breach is unlikely to result in a risk to the rights and freedoms of individuals. Frameworks are available, such as the Mitre ATT&CK that provide a knowledgebase of TTP based on real world observations.
For example, through uploading a copy of your data and threatening to publish it. exploiting a known software or application vulnerability which has a patch available to fix it. The UKs independent authority set up to uphold information rights in the public interest,promoting openness by public bodies and data privacy for individuals. The UK GDPR requires you to regularly test, assess and evaluate the effectiveness of your technical and organisational controls using appropriate measures. Unit 42 security consultants leverage industry-leading Palo Alto Networks tools to jumpstart your investigation by gaining necessary visibility across your endpoint, network, cloud and third-party data. Thank you for requesting a download of this eBook. Unit 42 provides access to one of the worlds largest and most experienced threat intelligence teams. Accelerate user adoption. The UKs independent authority set up to uphold information rights in the public interest, promoting openness by public bodies and data privacy for individuals. We have established a personal data breach has occurred, but data has not been exfiltrated, therefore there are no risk to individuals. Automate control of security, configurations, and content, and then replicate changes in real time. However, it is common that attackers will attempt to either delete or encrypt your backup. Craft, monitor, and analyse online exams with confidence. We determine and document appropriate controls to protect the personal data we process. Entrust users with self-service tools and built-in controls to drive adoption while ensuring governance policies are met. If you determine there is no evidence of data exfiltration, the ICO may ask you to demonstrate what logs and measures you used to make this decision. Reduce ITs security burden. EduTech is a corporate LMS that leverages AI to develop micro-training programs and seamlessly deliver them to fit busy schedules and crowded workstreams. Microsoft licensing causing confusion? So how can you enable internal and external teams to collaborate securely? However, just because a personal data breach has occurred does not automatically mean you should notify the ICO. We use the, We ensure all relevant staff have a baseline awareness of attacks such as phishing. The Can you restore the personal data in a timely manner? Something special happens when your campus community comes together. Buy products through our global distribution network. following the principle of least privilege; risk assessments of membership into privileged groups; and. Harnessing the power of Cortex XDR, Unit 42 will conduct a Compromise Assessment of your environment, focusing on the early stages of ransomware by analyzing endpoint telemetry and hunting for indicators of compromise associated with sophisticated ransomware groups. Law enforcement play a fundamental role in protecting individuals and the ICO work closely with these agencies in providing a multi-agency response to ransomware. A partner-centric view of our eBooks, webinars, and best practices, just for you. Do we still need to notify the ICO? Copyright 2022 Palo Alto Networks. The NCSC vulnerability management guidance will support you in managing vulnerabilities within your estate. By submitting this form, you agree to our, Email me exclusive invites, research, offers, and news, Readiness findings and recommendations report, In-depth technical report of findings and recommendations. Ransomware is a type of malware that attempts to unlawfully encrypt files on a host computer system. Can an attacker access the device or repository that stores the backup? If you are using cloud backups, you should read the NCSC blog posts about protecting these backups Offline Backups in on online world and Cloud Backup options for mitigating the risk of ransomware. The most recent threat landscape report from the European Union Agency for Cyber Security (ENISA) has also assessed ransomware as the prime threat with cybercriminals increasingly motivated by monetisation. This means once you have established a personal data breach has occurred, you should undertake a formal risk assessment. Our interactive, one-day workshops will help guide you through the pitfalls of data governance, sustainable adoption, and migration. We have recently seen an increase in phishing emails coming into our organisation and are looking at what measures we can put in place to mitigate this risk. This is usually done by a decryption key that only the attacker can access. You should also consider the terminology within the UK GDPR. Stay focused on what matters: enabling new and better ways of learning. You are required to notify the ICO of a personal data breach without undue delay and no later than 72 hours after having become aware of it, unless the breach is unlikely to result in a risk to the rights and freedoms of individuals. Frameworks are available, such as the Mitre ATT&CK that provide a knowledgebase of TTP based on real world observations.